Symantec Mobile Threat: Attackers Can Manipulate Your WhatsApp and Telegram Media Files
New research by Symantec reveals a Media File Jacking flaw affecting WhatsApp and Telegram for Android
WhatsApp and Telegram media files could be exposed and manipulated by malicious actors according to new research by Symantec’s Modern OS Security team, focused on the protection of mobile endpoints and operating systems. The security flaw, dubbed “Media File Jacking”, affects WhatsApp for Android by default, and Telegram for Android if certain features are enabled. It stems from the lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface (UI) for users to consume. This critical time lapse presents an opportunity for malicious actors to intervene and manipulate media files without the user’s knowledge. If the security flaw is exploited, a malicious attacker could misuse and manipulate sensitive information such as personal photos and videos, corporate documents, invoices, and voice memos. Attackers could take advantage of the relations of trust between a sender and a receiver when using these IM apps for personal gain or to wreak havoc.
However, as we’ve mentioned in the past, no code is immune to security vulnerabilities.
The Media File Jacking threat is especially concerning in light of the common perception that the new generation of IM apps is immune to content manipulation and privacy risks, thanks to the utilization of security mechanisms such as end-to-end encryption. Users generally trust IM apps such as WhatsApp and Telegram to protect the integrity of both the identity of the sender and the message content itself. This is in contrast to older apps/protocols such as SMS, which are known to be spoofed pretty easily. However, as we’ve mentioned in the past, no code is immune to security vulnerabilities. While end-to-end encryption is an effective mechanism to ensure the integrity of communications, it isn’t enough if app-level vulnerabilities exist in the code. What the Media File Jacking research we found demonstrates is that attackers may be able to successfully manipulate media files by taking advantage of logical flaws in the apps, that occur before and/or after the content is encrypted in transit.
We explore Media File Jacking, how it can be exploited, and its potential impact in more detail below.
Technical background
Android apps can store files and data in two storage locations: internal and external storage. Files saved to internal storage are accessible only by the app itself, meaning other apps cannot access them. Files saved to an external storage public directory are world-readable/writeable, so they can be modified by other apps or users beyond the app's control. According to Android developer documentation, “internal storage is best when you want to be sure that neither the user nor other apps can access your files.” By contrast, “external storage is the best place for files that don't require access restrictions and for files that you want to share with other apps or allow the user to access with a computer.”
By default, WhatsApp stores media files received by a device in external storage, in the following path: /storage/emulated/0/WhatsApp/Media/. In Telegram, if a user enables the “Save to Gallery” feature, under the assumption that this is safe and without understanding its indirect ramifications, Telegram will similarly store files in: /storage/emulated/0/Telegram/. Both are public directories. The apps load the received files from the public directories for users to see in the chat interface, when they enter the relevant chat.
The fact that files are stored in, and loaded from, external storage without proper security mechanisms (see more on this under “How app developers can protect against the threat” below), allows other apps with write-to-external storage permission to risk the integrity of the media files. Write-to-external storage (WRITE_EXTERNAL_STORAGE) is a common permission requested by Android apps, with over a million apps in Google Play having this access. In fact, based on our internal app data, we found nearly 50% of a given device’s apps have this permission.
When we researched the flow of how media files are handled in WhatsApp and Telegram, we found that in the time between when files are first received on a device and written to the disk (STEP 1), and when they are loaded for users to consume via the apps (STEP 3), the ideal opportunity for exploitation arises: malware can instantaneously analyze and manipulate the files (or just replace them with the attacker’s chosen files) for malicious gain (STEP 2).
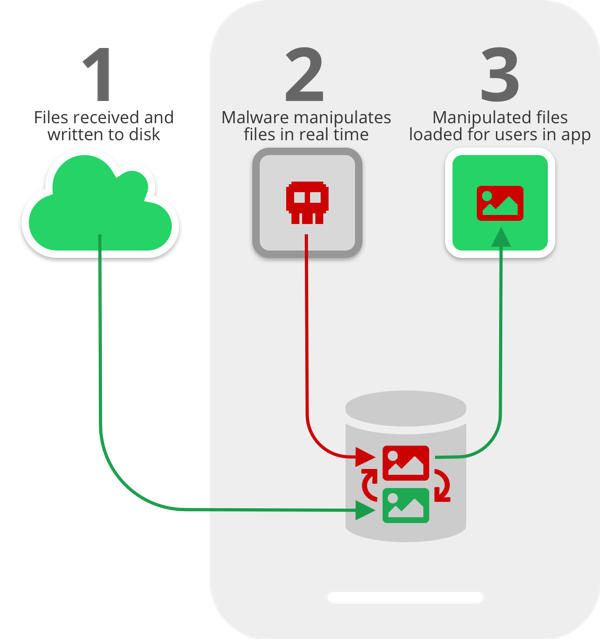
Think of it like a race between the attacker and the app loading the files. If the attacker gets to the files first - this can happen almost in real time if the malware monitors the public directories for changes - recipients will see the manipulated files before ever seeing the originals. Moreover, the thumbnail that appears in the notification that users see will also show the manipulated image or file, so recipients will have no indication that files were changed. Additionally, data can be manipulated on WhatsApp both when sending files - meaning the attack is launched on the sender’s device - and when receiving files - with the attack happening on the receiving device.
As discussed, the WRITE_EXTERNAL_STORAGE permission is very common among Android apps and users generally don’t hesitate to grant the permission as part of the on-boarding process. It’s therefore possible a user could unknowingly install the aforementioned malware as opposed to installing another app that asks for more aggressive permissions (such as critical device sensors or resources access) - in this case, a user may be more cautious before agreeing to install.
Additionally, the Media File Jacking vulnerability points to a bigger issue of app developers’ non-secure use of storage resources. In 2018, researchers discovered a similar flaw related to how some Android apps utilize external storage, opening the door to data manipulation by attackers. A so-called Man-in-the-Disk attack can occur when developers fail to take security precautions when storing files in external storage. It can result in silent installation of potentially malicious apps and denial of service for apps.
Impact
Let’s look at a few scenarios where attackers could exploit this vulnerability to scam victims:
1. Image manipulation. In this scenario a seemingly innocent, but actually malicious, app downloaded by a user can manipulate personal photos in near-real time and without the victim knowing. The app runs in the background and performs a Media File Jacking attack while the victim uses WhatsApp. It monitors for photos received through the IM app, identifies faces in the photos, and replaces them with something else, such as other faces or objects. A WhatsApp user may send a family photo to one of their contacts, but what the recipient sees is actually a modified photo. While this attack may seem trivial and just a nuisance, it shows the feasibility of manipulating images on the fly. In a similar scenario with wider-reaching consequences, the media files of a politician running for office or a company executive could be manipulated, allowing attackers to extort or frame targets.
2. Payment manipulation. In one of the most damaging Media File Jacking attacks, a malicious actor can manipulate an invoice sent by a vendor to a customer, to trick the customer into making a payment to an illegitimate account. As in the previous scenario, an app that appears to be legitimate but is in fact malicious, watches for PDF invoice files received via WhatsApp, then programmatically swaps the displayed bank account information in the invoice with that of the bad actor. The customer receives the invoice, which they were expecting to begin with, but has no knowledge that it’s been altered. By the time the trick is exposed, the money may be long gone. To make matters worse, the invoice hack could be broadly distributed in a non-targeted way, looking for any invoices to manipulate, affecting multiple victims who use IM apps like WhatsApp to conduct business.
3. Audio message spoofing. In this scenario, an attacker exploits the relations of trust between employees in an organization. A CEO sends his CFO an audio message, via WhatsApp, requesting updated slides for a board meeting next week. The attacker, using voice reconstruction via deep learning technology – something that is becoming more and more feasible today – alters the original audio file to communicate to the CFO, in the CEO’s own voice, that a payment needs to be transferred immediately to a fictitious party, which is in fact the attacker. The bad actor not only manipulates the communications of the CEO, but goes a step further to reconstruct his voice, resulting in a very effective deception technique. The original message from the CEO is replaced when it arrives at the CFO’s phone. What the CFO hears in the end is a credible audio message from his boss to make a payment, something that can easily be perceived as a legitimate request by an unaware employee.
4. Another interesting example where we might encounter a Media File Jacking attack is fake news. In Telegram, admins use the concept of “channels” to broadcast messages to an unlimited number of subscribers who consume the published content. An attacker can change the media files that appear in the channel feed in real time. Let’s consider, for example, a trusted news network that maintains a Telegram channel. Subscribers rely on the channel to get credible news. An attacker can communicate falsities in the channel by manipulating the media files received there. Interestingly, this can happen without the knowledge and consent of both the channel owner and the end-victim. This example illustrates how both the sender and receiver can be harmed by the attack: receivers consume fake news and the channel owner’s reputation or credibility takes a hit.
How app developers can protect against the threat
As previously mentioned, WhatsApp saves files to external storage automatically, while Telegram does so when the “Save to Gallery” feature is enabled. In both cases, however, neither apps have any measures in place to protect their users from a Media File Jacking attack.
To ensure that media files are kept safe from malicious actors, we recommend the following measures:
- Validate the integrity of files: Store in a metadata file a hash value for each received media file before writing it to the disk. Then, confirm that the file has not been changed (i.e. the hash is the same) before the media file is loaded by the app in the relevant chat portion for users to see. This step can help developers validate that files were not manipulated before they are loaded. This approach balances between the security (protection against Media File Jacking attacks) and functionality (e.g., supporting third party backup apps) needs of the IM apps.
- Internal storage: If possible, store media files in a non-public directory, such as internal storage. This is a measure some IM apps have chosen.
- Encryption: Strive to encrypt sensitive files, as is usually done for text messages in modern IM solutions. This measure, as well as the previous one, will better protect files from exposure and manipulation. The downside is that other apps, such as photo backup apps, won’t be able to easily access these files.
With the release of Android Q, Google plans to enact changes to the way apps access files on a device’s external storage. Android’s planned Scoped Storage is more restrictive, which may help mitigate threats like the WhatsApp/Telegram flaw we found. Scoped Storage means that apps will have their own storage area in an app-specific directory, but will be prevented from accessing files in the entire storage partition, unless an explicit permission is granted by the user. While this promises to improve user privacy protection, it also includes major changes to the way millions of applications utilize external storage. Partially because of these challenges, Google recently announced that it plans to push the API’s enforcement only in 2020, in the next major platform release. Even then, the impact of the enforcement will take time due to the version fragmentation of the Android operating system.
Disclosure Process
Symantec notified Telegram and Facebook/WhatsApp about the Media File Jacking vulnerability.
Protection
Symantec’s malware detection engines, which power Symantec Endpoint Protection Mobile (SEP Mobile) and Norton Mobile Security, detect apps that exploit the described vulnerability.
As such, enterprises and consumers leveraging SEP Mobile and Norton Mobile Security respectively, benefit from the engines’ deep analysis of apps and detection of malicious, suspicious and unwanted behavior, and are already protected from the described threat.
Mitigation
Disabling the storage of media files in external storage
IM app users can mitigate the risk Media File Jacking by disabling the feature that saves media files to external storage. We show how to do this in WhatsApp and Telegram below.
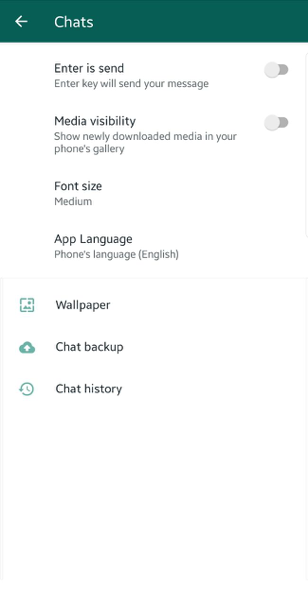
WhatsApp: Settings -> Chats -> Media Visibility
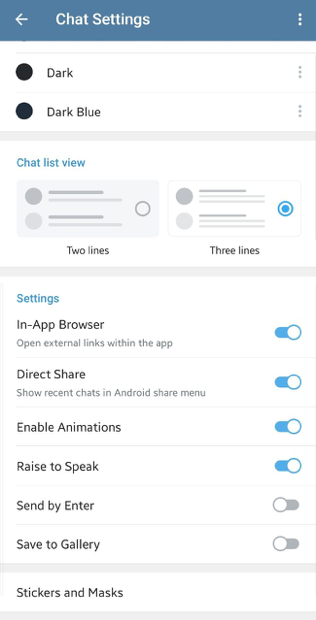
Telegram: Settings -> Chat Settings -> Save to Gallery

Symantec Mobile Threat Defense: Reducing Risky App Threats with Robust App Vetting
SEP Mobile, with integrated best-of-breed app analysis from Appthority, provides enterprises the most complete protection against mobile threats










We encourage you to share your thoughts on your favorite social platform.