Secure Access Service Edge (SASE) or Zero Trust?
What you should consider when evaluating a SASE architecture for your business
In a previous blog we introduced the SASE (Secure Access Service Edge) architecture, a new architecture fit for the distributed, mobile and cloud enabled organization.
This SASE architecture combines networking capabilities to enable connectivity for any user, from any device, anywhere together with security capabilities to enforce the organization security policies on that access. Eventually resulting in a Secure Access platform enabling the organization to securely connect any user, from any device, anywhere to any resource.
The SASE architecture is designed to enable the enforcement of security at the network level (similar to traditional firewall or IPS solutions). Other approaches don’t rely on network for security enforcement, but rather on SaaS vendor capabilities or endpoint based enforcement. They may also lack capabilities at best and at worst - could be unsecure (BYOD or hosted applications with minimal security controls). The SASE architecture allows enforcing uniform security across all corporate resources and user's activities regardless of the endpoint or SaaS vendor capabilities.
This architecture also enables visibility into user's actions, which is a mandatory requirement for detection as well as forensics and compliance.
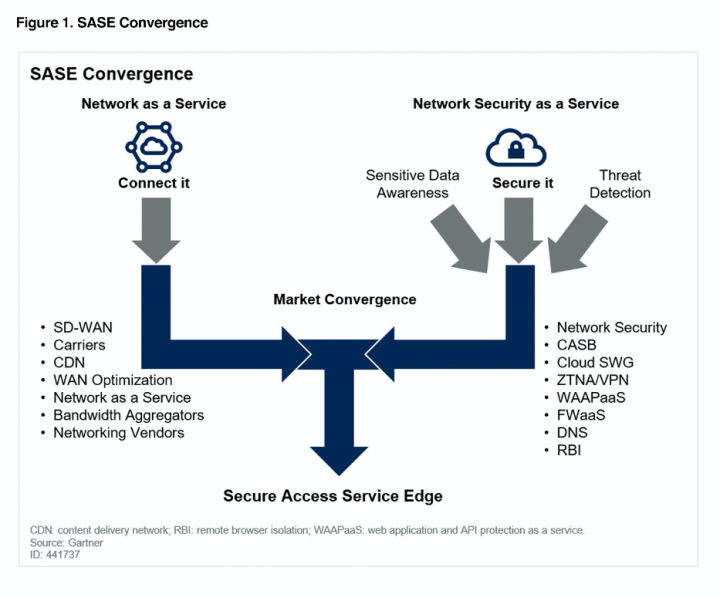
***Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available here.***
In this post we will focus on what are the security capabilities required to enable the Zero Trust model in order to secure your corporate data, what SASE components are in action and what you should consider when evaluating a SASE architecture for your business.
What is Zero Trust?
Zero Trust was a term coined in 2010. This term refers to an approach where nothing (including the corporate network, users or devices) should be trusted, assuming each of these entities could have been breached and used to steal sensitive data.
The Zero Trust model puts the data at its center and references multiple controls which should be involved in determining whether a specific entity should be allowed access to a specific resource/data. These controls should also allow visibility into the user's activities to enable detection and behavior analytics to determine the risk the user imposes to the resources and data. (or in other words - the chances an account has been compromised).
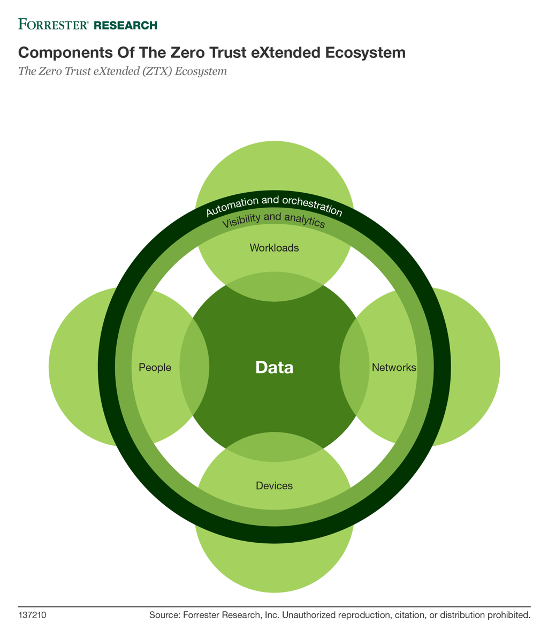
These controls are centered around the identity of the client (user or service), the device and the data (workload or network). An example set of controls include:
- the risk score of the user
- authentication method (FIDO, MFA, etc.)
- organizational role
- device risk and status (managed vs. unmanaged)
- location
- eventually the data context (confidential, PII, PCI, etc.)
In order to successfully implement this model across the data in the modern enterprises which is spread across SaaS, IaaS and PaaS and hosted/on-premises environments the SASE architecture must satisfy several requirements.
What components in SASE enable Zero Trust?
Given the Zero Trust model is enabled around data controls and visibility to corporate resources the 2 main components which are providing this capability is the CASB (Cloud Access Security Broker) solution, used to access SaaS resources and the ZTNA (Zero Trust Network Access) solution, used to access IaaS/PaaS and hosted/on-premise resources.
These 2 solutions should allow controlling user's activities based on user context, device context (health, location, etc.) and data as previously described. However, this is harder than it sounds. Most of the VPN/Remote Access solutions today are still focusing on network access, providing a true/false verdict on a full network access request (VPN connect event) by the users.
The visibility into the user’s actions and the data being accessed is also critical to a successful implementation of a Zero Trust model.
Restricting access to specific resources based on user and device risk, status and role is not the only requirement. The visibility into the user’s actions and the data being accessed is also critical to a successful implementation of a Zero Trust model.
To allow the implementation of the Zero Trust model both CASB and ZTNA solutions must have the ability to provide Layer7 (application layer) visibility, allowing the control of user's actions (upload, download, modifying content, etc.), integration with DLP (as the data is visible to these solutions) and full visibility into user’s actions for detection, forensics and compliance.
These solutions should also be able to integrate with your existing IAM investments such as your directory services (Azure AD or Okta) and MFA as well as provide built-in capabilities such as UEBA, sandboxing and anti-malware capabilities.
What does Symantec offer?
Symantec, a division of Broadcom (NASDAQ: AVGO), offers CloudSOC, a market leading CASB solution enabling secure access to SaaS resources and Secure Access Cloud, an innovative ZTNA solution, from Symantec’s acquisition of Luminate Security. These enable secure access to on-premise, hosted and IaaS/PaaS based resources
Both solutions provide the ability to enforce access and activity controls based on the context of the user and the device, built-in integration with Symantec's DLP as well as the ability to integrate with all leading Directory Service and IDaaS solutions.
These 2 solutions, combined together, provide Layer7 secured connectivity to corporate resources anywhere, while enabling the controls and visibility required by the Zero Trust model.
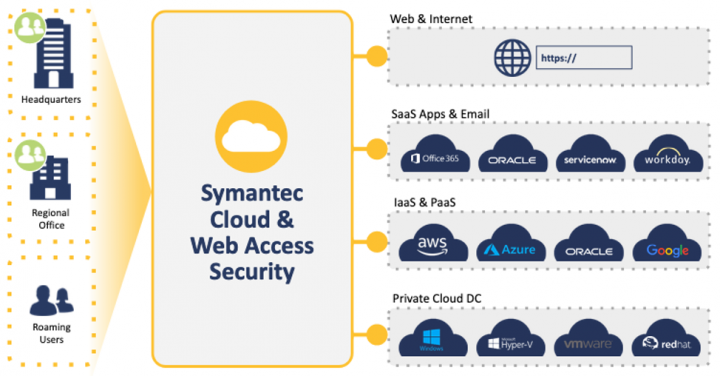
With the addition of the Secure Web Gateway solution, Symantec offers a comprehensive SASE platform, while helping you drive the implementation of a Zero Trust model in your organization.
What Next?
To summarize, the shift of enterprises to modern architecture centered around cloud and mobile, requires a modern security architecture to enable the business to securely leverage their new investments.
The SASE architecture is becoming this modern architecture to allow both security and connectivity for the modern enterprise.
In turn, the Zero Trust model is the de-facto security model which should be supported and implemented by the controls available in the SASE architecture.
Therefore, it is critical to evaluate the capabilities of the vendors in your SASE architecture for their ability to implement a Zero Trust model.
SASE and Zero Trust are NOT mutually exclusive, on the contrary, they're supplementing each other and one should be used to enable and drive the other.

Symantec Information Security: Innovation and Strategy for Your Success
Join to learn: - How Symantec’s Enterprise Division is addressing key customer challenges across advanced threats, privacy and compliance & digital transformation - How Symantec’s Information Security vision and strategy benefits customers invested in CloudSOC CASB, DLP, Secure Access Cloud, Compliance and Encryption








We encourage you to share your thoughts on your favorite social platform.