Security for the Evolving Enterprise
Symantec helps organizations transition to the cloud at their own pace with flexible management options and full visibility over enterprise hygiene
The number of customers adopting a cloud-first strategy is growing, with a large percentage of organizations looking to reduce the cost of maintaining an on-prem management infrastructure. These organizations are moving to SaaS-based offerings for managing the security posture of their environment. According to the 2018 IDG Cloud Computing study, 73% percent of organizations have at least some portion of their infrastructure already in the cloud, and within 18 months, the number of environments that are non-cloud will decrease from 53% to 31%. Gartner predicts that various forms of cloud computing are among the areas where most CIOs will increase investments in 2020.
While enterprises seek to move their management to a SaaS based offering, large enterprises may need time to plan and execute such a move. Migration often involves major workflow changes, adoption barriers, and other technical and non-technical challenges. Many enterprises choose to move only a subset of devices to a cloud-managed solution, for example: devices of roaming users or employees who may become part of another company as a result of a merger or acquisition – these devices can be easily managed via a SaaS solution. This may be a preferred option compared to standing up a brand new on-prem management infrastructure. Organizations can still keep a portion of their endpoints managed via on-prem management, but the ability to use both SaaS and on-prem options makes a hybrid model more appealing for such environments.
As Gartner notes, “cloud first” doesn’t mean “cloud always.” Solutions that offer an “all or nothing” model – forcing organizations to manage their infrastructure all via cloud or on-prem – do not provide enterprises with the flexibility to try out and gradually move to a SaaS based model. No matter where you are in the process, your endpoint security solution should accommodate your management needs, not the other way around.
Organizations can still keep a portion of their endpoints managed via on-prem management, but the ability to use both SaaS and on-prem options makes a hybrid model more appealing for such environments.
In the face of today’s evolving threats, enterprises are struggling with the increasing cost and complexity of endpoint security management. Misconfigurations in protection capabilities, unpatched vulnerabilities and poor enterprise hygiene can expose you to targeted attacks. Maintaining a good enterprise hygiene is critical for achieving the highest level of protection. At Symantec, we support the management option that helps you best tune policies and gives you full visibility to ensure optimal capabilities are enabled in your environment.
According to the Ponemon Institute, in 2017 organizations had an average of seven different software agents installed on their endpoints, resulting in noisy and time-consuming management. Symantec solves this problem for customers by deploying a single agent across all endpoints. Admins no longer need to worry about separate client installations, thereby lowering management complexity and total cost of ownership. One unified installation package is available for all clients, delivering our full endpoint protection stack: Attack Surface Reduction, Endpoint Protection, Detection and Response, along with Data and Web Protection via the DLP and WSS agent integrations. The single-agent architecture covers both traditional and modern endpoints, including iOS, Android, Windows in S mode and Windows on Arm.
Management options for transitioning organizations
Protection and management capabilities are important for maintaining a good security posture as you transition to the cloud. One management approach may be more beneficial than another, depending on your needs:
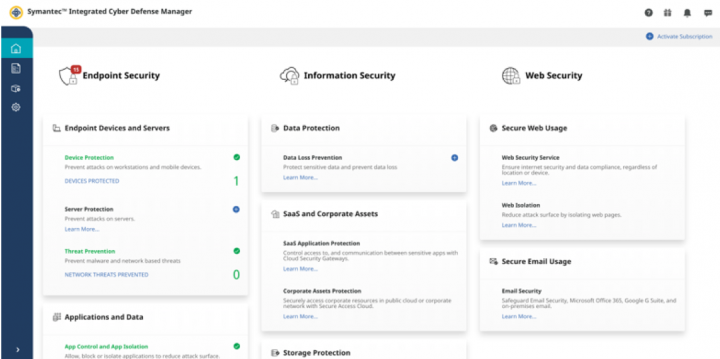
- Cloud/SaaS: The cloud-based approach is ideal for organizations seeking to eliminate the operational overhead associated with managing an on-prem infrastructure. Symantec’s Integrated Cyber Defense Manager (ICDm) provides real-time visibility and control over threats, policies, and incidents, from multiple Symantec solutions, in a single console. This helps speed up response time to real time. No more heartbeat intervals, and no need to wait for your endpoints to connect back into your network to see what threats are affecting them. You also no longer have to back up data and setup DB replication schedules. Beyond those benefits, ICDm provides the ability to scale as your organizational needs grow, without having to invest and rebuild hardware. A few hundred endpoints that come in through an acquisition for example, can be easily onboarded and brought into compliance without having to deploy any additional network and management infrastructures. Simply deploy the Symantec agent from ICDm and you’re ready to go.
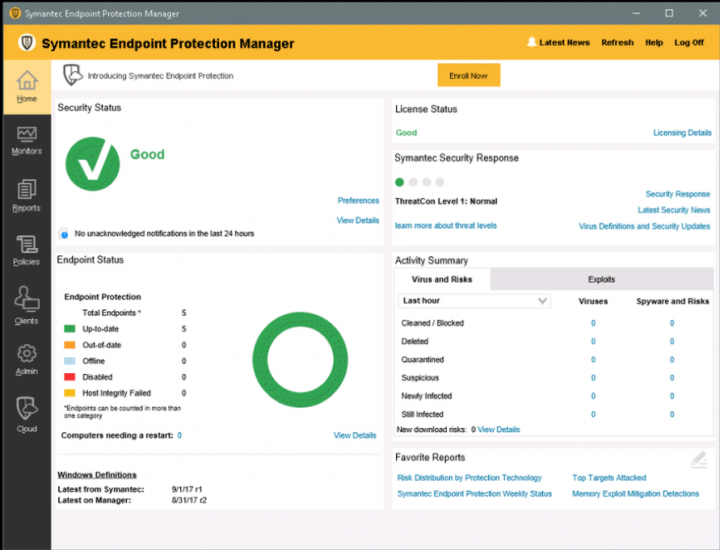
- On-prem: This is where most enterprises are today. They continue to use an on-prem architecture as it allows them to piggyback on their existing infrastructure. On-prem also allows customers with strict compliance and regulatory needs to have more control over their data and where they host their management. This option is better suited to restricted networks, for example a factory in a remote location which doesn’t have outbound connectivity or an air-gapped environment in a research facility. The on-prem management console is feature rich with several policy and configuration settings, and years of development work built into it. It provides robust investigation and incident response capabilities for security admins and SOC analysts, including visibility into red team tests. This helps prevent advanced zero-day threats and lateral movement attacks. Customers especially benefit from the management console’s flexibility and granular controls.
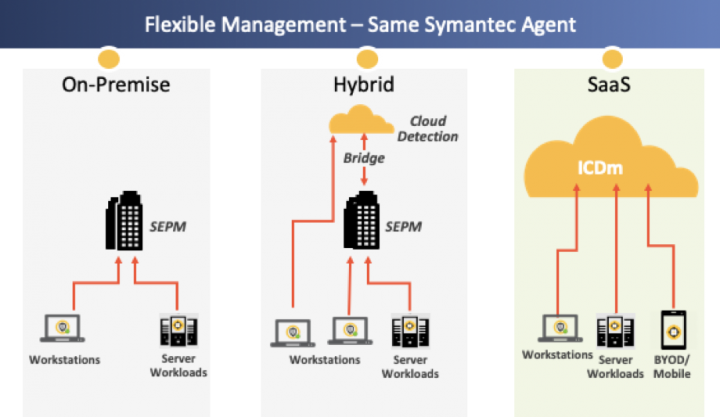
- Hybrid: Symantec Endpoint Security customers have traditionally maintained their servers and databases on-prem. However, many of them are now starting to move their data centers to the cloud and are also looking to move their endpoint security management infrastructure. As mentioned before, transitioning to a new management solution is a difficult process which doesn’t happen overnight. This is where the hybrid model comes in, providing the most flexibility for customers who want to move to a cloud-managed console gradually. Administrators can pick and choose the set of machines they want to move to cloud management, and continue doing so over a gradual period of time while maintaining part of their environment untouched. The architecture allows for full visibility over devices, events and alerts in a single place, our Integrated Cyber Defense manager.
Enterprise hygiene
A key aspect of deployment management for an evolving and heterogeneous enterprise is ensuring good enterprise hygiene, to maintain device protection and policy compliance. Symantec’s Admin Console provides visibility into the overall security posture in a single place, including the health of all endpoint devices, as well as tools to ensure that any new devices that join the network are identified and protected. Multiple methods are available to enroll endpoints:
- Discover & Deploy. Discover devices in your environment that are not protected by Endpoint Security using our network discovery, and then deploy the Symantec agent to them remotely from the cloud or your on-prem console. Network discovery performs a network level search for unmanaged devices. You assign one machine with the Endpoint Security agent to crawl the network and identify all the devices that don’t have the agent installed. The machine then reports back to the dashboard with a list of devices that are missing protection capabilities. You can also configure and use your Mobile Device Management (MDM) provider to get a list of all devices in the environment. Once devices appear as unmanaged, you can enroll them with push enrollment right from the console without having to deploy agents separately. The Discover and Deploy method might be preferred if you have a large number of unmanaged devices in your environment, and you need help identifying them, or even in cases where an admin wants to continuously monitor for new unprotected devices coming into the network.
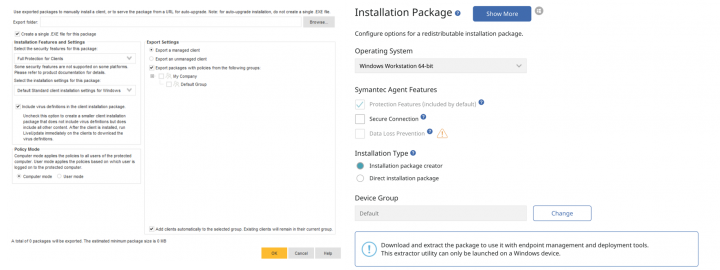
- Ability to create a redistributable installation package. This method makes it easier for you to use your existing third-party deployment suite for enrollment. You create a redistributable installation package that can be delivered through systems such as Active Directory GPO, Symantec IT Management Suite, VM Workspace ONE, etc. You can also use the downloaded package to install the agent directly onto a device.
- Ability to invite users via email. This method allows you to send your end users an email with a link to download the agent directly onto their devices. You might choose this option for enrollment of remote employees or if you don’t have a deployment suite.
- Simplified content distribution. With Endpoint Security, you no longer need to worry about redeploying an agent on endpoints to have the latest version. Our solution can automatically push upgrades for software versions and agent content. Once you set your Content Policy and schedule in the cloud console, they will automatically be distributed to devices via our LiveUpdate feature.
- Reporting. The console reports on client health and provides metrics on misconfigured or malfunctioning clients. You can review the health of your client-to-management console connection and which devices are and aren’t protected, including which devices are at risk. This information helps you manage agent health and configure policies to ensure proper operation of the Symantec agent. Regardless of which management option you’re using, Endpoint Security enables you to check and maintain proper agent hygiene.
Endpoint Security’s agent has built-in protection capabilities fit for each device its deployed on. Once the agent is installed, it is ready to protect devices against known and zero-day threats using the robust protection stack.
Easy upgrades for existing customers
Most customers I talk to are seriously considering the cloud or are in the process of migrating to it. These organizations have a large number of endpoints, policies and configurations to manage, and they likely prefer not to rebuild these once they transition over. If your organization is ready to move to cloud management, you can easily upgrade your existing policies and settings to the cloud. You can make your agents-cloud managed with a simple command, without having to deploy and reinstall another agent.
Here’s how it works in a nutshell. If you are using our on-premises Symantec Endpoint Protection product, cloud enabling your deployment is just a click away. You can connect it to the Integrated Cyber Defense manager, and we will automatically upload the device information. This process first involves selecting the devices that you want to be cloud-managed by issuing a simple command, and then either: using out-of-the-box default Symantec policies, customizing policies in ICDm, or exporting/importing selected policies from the on-prem manager.
* * *
Protecting your organization from advanced, evolving threats can be challenging – but managing your security solutions shouldn’t be. Symantec provides easy and flexible management options that fit organizations wherever they are, whether they have an on-prem, cloud-based, or hybrid infrastructure. Additionally, with an easy-to-deploy single agent, security teams can be confident their endpoint security scales as they scale.

Symantec Named a Leader
In 2019 Gartner Magic Quadrant for Secure Web Gateways and the 2019 Magic Quadrant for Cloud Access Security Brokers








We encourage you to share your thoughts on your favorite social platform.