Symantec Mobile Threat Defense: A Snapshot of Mobile Security Incidents in Q2 2019
Threats associated with risky apps, iOS-device hacking and mobile phishing were among the major incidents
App vulnerabilities and malware accounted for a large part of mobile threats that made headlines in Q2.
Symantec’s Modern OS Security team saw spyware affecting the popular Instant Messaging (IM) app WhatsApp, enterprise apps gaining unwarranted access to user data, and several categories of Potentially Harmful Apps (PHAs) reportedly hiding in the Google Play Store. Beyond app risks, new phishing techniques revealed holes in mobile browser protection.
As part of our quarterly threat recap series (see the previous quarter’s recap here), we review some of these noteworthy mobile security incidents below.
WhatsApp Flaw Opens Encrypted Communications
A WhatsApp vulnerability discovered in May, which has since been patched by engineers, reportedly let hackers break into the secure communications of iPhone and Android users. Security researchers said they found spyware – reportedly associated with cyber-intelligence company NSO Group, the makers of the Pegasus spyware – that exploits the WhatsApp flaw. Hackers could remotely insert malicious code and steal sensitive data from mobile devices just by placing a WhatsApp call, even if victims don’t answer. In a statement, WhatsApp said the vulnerability exists in older versions of the app and encouraged users to upgrade to the latest version, which includes the most recent security fix. However, users of older versions may still be at risk of compromise.
Symantec Endpoint Protection Mobile (SEP Mobile) protects against this vulnerability (CVE-2019-3568) by allowing customers to set a rule in their unwanted apps policy. According to the rule, older WhatsApp versions that are vulnerable to the bug will be flagged as risky.
OAuth Misuse Could Risk Corporate Data in G Suite apps
Researchers from Symantec's Modern OS Security team released new research in April showing that many enterprise iOS and Android apps are misusing the OAuth authorization protocol to obtain sensitive, persistent access to data in G Suite services such as Gmail, Google Drive, and Google Calendar. These apps can continue accessing personal or corporate data in Google, even if they are uninstalled from the device, as long as their access is not revoked, and even when users are offline.
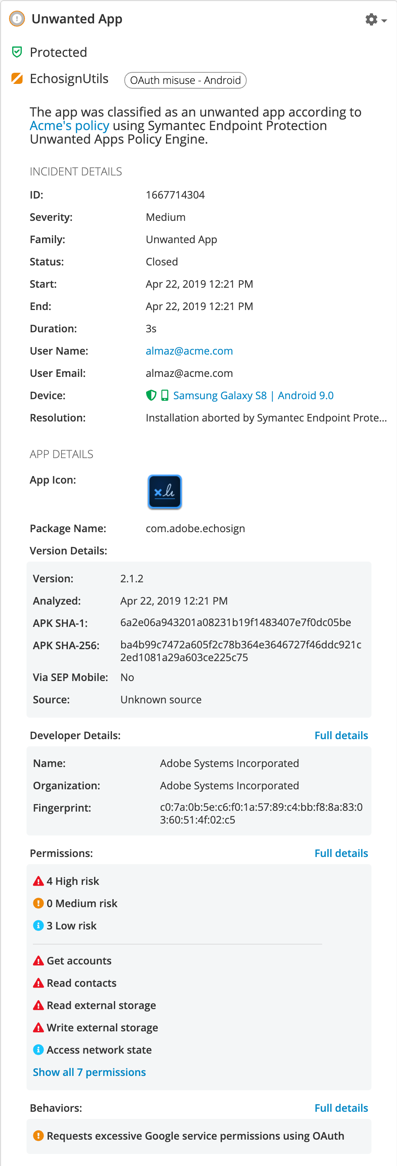
In June, Google announced an improvement to its G Suite OAuth Token Audit API which can help mitigate OAuth misuse. The improvement gives enterprises more visibility and control over how third-party apps utilize G Suite APIs they’ve been granted. Essentially, admins can better see which apps have unauthorized access as well as what data they can access and when. Based on this, admins can revoke access tokens if necessary.
In addition to these improvements, SEP Mobile customers can protect against apps misusing OAuth by leveraging the recommended unwanted app policies.
Forensics Company says Commercial Product can Break into any iOS device
A commercial tool manufactured by Cellebrite, a mobile device forensics company, can break into any iPhone or iPad running any iOS version, including the newest iOS 12.3.2 release, the company announced in June. Cellebrite says the product is intended for law enforcement use, allowing investigators to extract data from locked smartphones. The story is yet another example of how mobile devices and operating systems are not immune to vulnerabilities, even with the latest releases and security improvements. According to Forbes, Cellebrite devices have sold on eBay for as little as $100, making them easily available to hackers and putting the world's 1.4 billion iOS users at risk of attack.
Frost & Sullivan: Hackers can Exploit Barriers between Mobile and Traditional security
Silos between mobile security and traditional security deployments in enterprise can leave holes for hackers to exploit, Frost & Sullivan analysts write in an executive brief on "The Evolution of Mobile Security." While organizations invest resources to secure traditional endpoints, mobile device protection is not given the same consideration. This can be a detriment to the overall security posture, as modern endpoints can make up 50% of endpoints that access corporate data in an organization, according to the brief. Additionally, analysts say that to provide a better defense against mobile attacks, organizations need to advance to “Tier Three” mobile security solutions that provide more holistic security configurations.
Android Year in Review 2018: Click Fraud, Malware, Other harmful Apps Found in Google Play
Google's annual Android Security & Privacy Year In Review found that Potentially Harmful Apps were installed from Google Play in 2018, among them click fraud apps, malware, SMS fraud, and spyware. The report also found that devices installing apps from pirate app stores were exposed to PHAs eight times more often than devices downloading apps from the official Google Play Store. Despite Android security improvements, risky apps still manage to bypass Google’s vetting mechanism and sneak into the Play Store.
Phishing threats Reveal Protection Gaps in Popular Mobile Browsers
In April, developers found an exploit in Chrome for mobile that displays a fake address bar which won’t disappear until users visit another site. Attackers can even create a page that can prevent users from seeing the real address bar when they scroll up. Additionally, research by the Laboratory of Security Engineering for Future Computing, found that mobile browsers protected by Google’s anti-phishing mechanism failed to detect any phishing sites between mid-2017 and late 2018. The research revealed that URL blacklisting did not function as intended in popular mobile browsers, such as Chrome, Safari, and Firefox, leaving users of these browsers vulnerable to phishing.
The above incidents make up a sample of Q2’s major mobile security headlines. Other incidents worth mentioning include: last month’s confirmation by Google that an advanced backdoor came preinstalled on Android devices; the inadvertent leaking of SmartThings source code and secret keys by a Samsung lab; and an announcement by Google that only 10% of Android devices are running the latest version of Android Pie months after its release. These stories, and the growing frequency and sophistication of mobile attacks, serve as a reminder of the importance of implementing effective security solutions, including across mobile endpoints, to protect enterprise data.

How to Effectively Secure Hundreds of Thousands of Mobile Devices
Join us as we cover ways to effectively and efficiently secure mobile devices across a broad range of industries.

Symantec Mobile Threat Defense: A Snapshot of Mobile Security Incidents in Q1 2019
From the FaceTime bug to risky apps leaking millions of sensitive files from employee devices – mobile security threats kept us busy this quarter








We encourage you to share your thoughts on your favorite social platform.